
Cover photo by Matias Mango
Data security startups play an important role in protecting corporate sensitive information and ensuring compliance with data privacy regulations.
Startups offer tools and solutions tailored to the various data security needs of corporations. Among the most common needs are preventing data breaches and security threats, protecting sensitive data from unauthorized access, maintaining data privacy and compliance with regulations, enabling secure data collaboration and analysis, and preparing secure data security infrastructures for future development needs.
By adopting some successful startup solutions, corporations aim to share the risk of creating new solutions with startups, which helps preserve their brand reputation and ensure the security and privacy of their customers' data.
Let's examine why data security startups focusing on different needs are important for corporate clients.
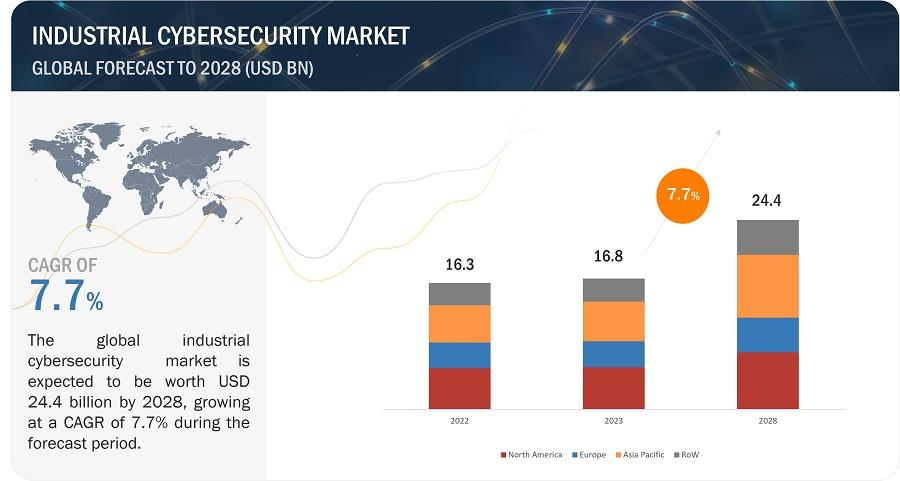
Industrial Cybersecurity Market
1. Decentralized Digital Identity
These startups eliminate dependency on central authorities by developing technologies for users to own and control their digital identities. Decentralized digital identities enhance data freedom for users, increase privacy, and reduce the risk of identity theft.
Startup Example: Midy
Founded under the name Evernym, this startup was later acquired by the security giant Avast and continued its journey as Midy. Its value proposition lies in enabling e-commerce companies to verify customer identities and conduct accurate analyses.
2. Data Governance
Data governance solutions support regulatory compliance, data breach prevention, and data-driven decision-making. Startups focusing on this area develop tools and solutions for organizations to effectively manage, organize, and protect their data.
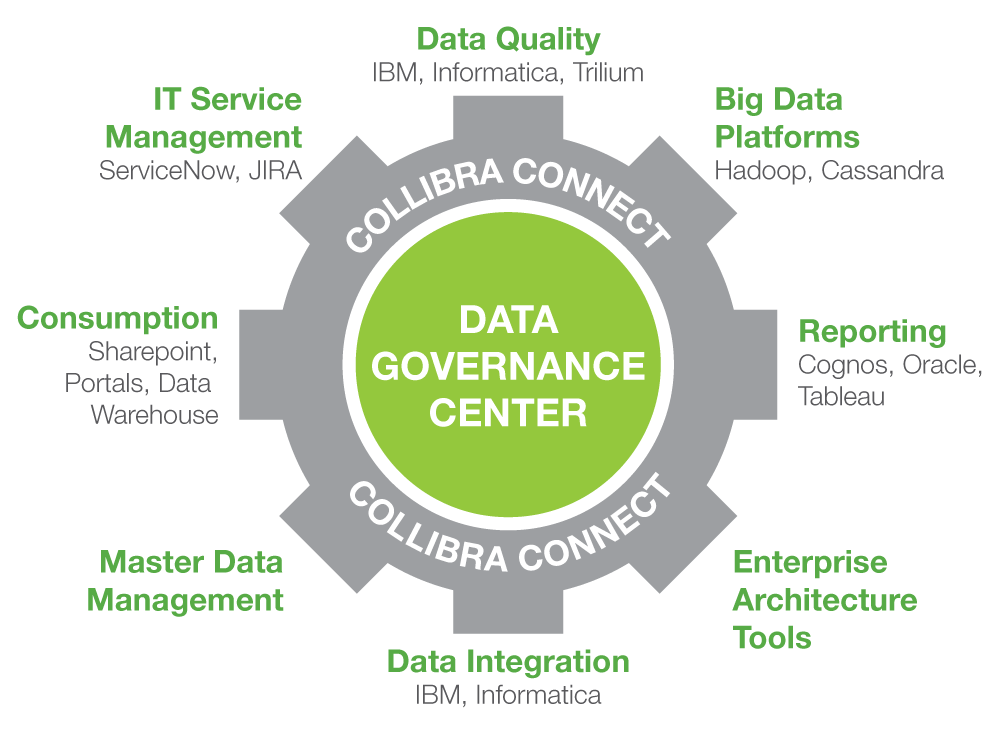
Startup Example: Collibra
Collibra's solution is a data governance platform serving enterprise clients for data management and business intelligence. It accelerates companies' understanding of their data and improves decision-making.
3. Data Masking
Data masking startups reduce the risk of data breaches by protecting sensitive information during new project development and testing phases.
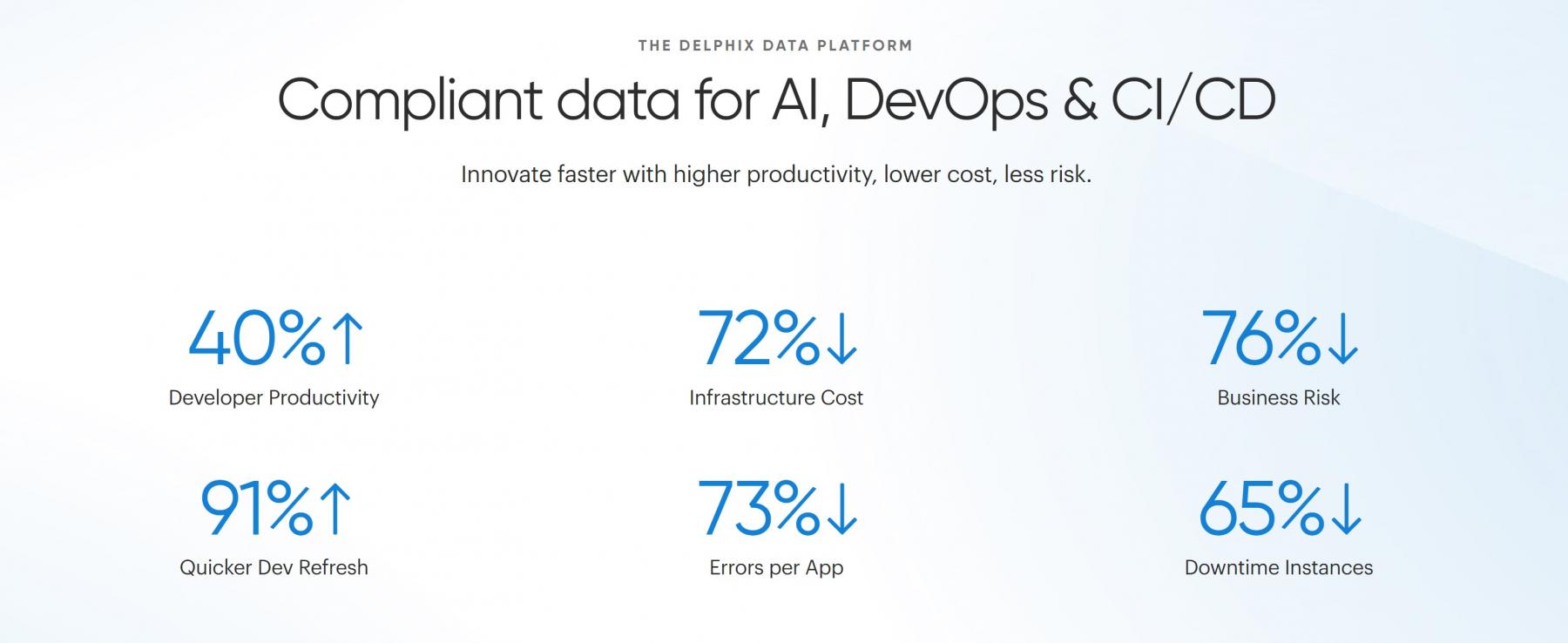
Startup Example: Delphix
Delphix enables Oracle and other SQL Server clients to copy databases with minimal storage requirements.
4. Synthetic Training Data
Synthetic training data allows the development of artificial intelligence models without the need for real data, ensuring privacy protection. By generating artificial data resembling real data, these startups enable the training of AI models without compromising privacy.
Startup Example: DataGen
DataGen provides a platform for generating synthetic data to secure solutions in virtual reality, augmented reality, artificial intelligence, autonomous vehicles, robotics, and IoT.

5. Data Loss Prevention (DLP)
DLP solutions protect against unauthorized data leaks by monitoring and controlling data movement within an organization, preventing data breaches, and ensuring compliance with regulations.
Startup Example: Endpoint Protector
Endpoint Protector focuses on stopping unintentional data leaks, protecting against malicious data theft, and providing sensitive control over portable storage devices.

6. Data Cleaning Rooms
Data cleaning room startups provide infrastructure for collaborative data analysis between two different entities without exposing sensitive information, supporting the creation of valuable insights and business intelligence while maintaining privacy.
Startup Example: Databricks Partner Data Exchange
Through Databricks data cleaning rooms, companies securely collaborate on data without compromising privacy or security.

7. Database Security
Startups offering database security solutions provide tools and solutions to protect databases from unauthorized access, data breaches, and other security threats, ensuring data integrity and ease of use.
Startup Example: Imperva
Like many data security startups acquired by defense and aerospace giant Thales Group, Imperva offers end-to-end data security solutions that protect critical applications, and APIs.
8. Post-Quantum Cryptography
Startups focusing on this area develop cryptographic algorithms and next-generation encryption solutions resistant to attacks from quantum computers, preparing data security for the future.
Startup Example: PQShield
PQShield supports product groups in transitioning from legacy encryption to quantum-safe standards, offering ready-made and custom IP for IoT hardware and software, PKI, server technologies, and end-user applications.
Many companies have achieved significant success by collaborating with data security startups. Here are two concrete examples:

Sanofi & Owkin: Sanofi invested $180 million in Owkin's artificial intelligence and federated learning solution to advance its oncology pipeline. The collaboration aims to create robust disease models while preserving the privacy of large datasets obtained from various research institutions and hospitals. (Sanofi invests $180 million equity in Owkin)
TELUS & Collibra: Telecommunications company TELUS partnered with Collibra to eliminate silos and centralize information about data assets in a data catalog, enabling teams to efficiently find and understand reliable data.(TELUS centralizes data assets with Collibra)

These success stories demonstrate that data security startups can help corporations achieve their data security goals. Data security is a risky area for every organization, and validated startups have proven to be structures best capable of sharing the risk. To validate their value propositions, startups need to work with numerous corporate clients and learn from their experiences. Working with startups who have validated value propositions means reducing risk by leveraging the learnings of many other startup corporate engagements. As the focus areas of data security expand, the market served by data security startup clusters continues to grow. We recommend that corporations consider integrating data security startup solutions into their corporate structure and processes. We manage the interaction of companies with external solutions through a service developed in collaboration with many companies, just like the data security startups mentioned above.